Critical D-Link NAS vulnerability under active exploitation

Cyble Global Sensor Intelligence observed active exploitation of critical D-Link Vulnerability
Recently, the security community has raised concerns regarding the vulnerabilities found in D-Link Network Attached Storage (NAS) devices. The vulnerabilities, identified as CVE-2024-3272 and CVE-2024-3273 were disclosed initially by an individual who goes by the alias “netsecfish” on GitHub on March 26, 2024. D-Link disclosed the same on April 4, 2024.
The March 26 GitHub post highlighted that the malicious HTTP request is aimed at exploiting the vulnerable endpoint of affected D-Link NAS devices, thereby generating significant interest within the cyber security community.
The severity of the issue can be understood from the fact that the Cyble Global Sensor Intelligence (CGSI) network detected ongoing exploitation attempts of these vulnerabilities from April 09 itself. This also indicates the swift weaponization of publicly available exploits by Threat Actors (TAs) targeting vulnerable internet-exposed D-Link NAS. The figure below depicts the exploitation attempts observed from one of the CGSI instances.
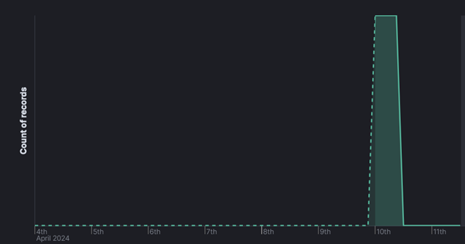
Figure 1 – Exploitation attempt of D-Link NAS vulnerabilities observed via CGSI Network
CGSI’s findings also indicate that the majority of these attacks are originating from China.
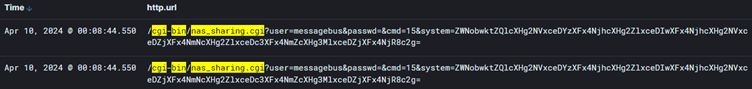
Figure 2 – Exploitation attempt observed by CGSI network
During routine monitoring of cybercrime forums, Cyble Researcher & Intelligence Labs (CRIL) observed a post on a prominent Russian cybercrime forum on April 8, 2024 about a Threat Actor (TA) sharing an exploit to target the vulnerable D-Link NAS instances affected with CVE-2024-3273.
To support the claims, the TA further shared the output of the successfully executed exploit on an instance deployed on localhost, along with output from the “id” command reflecting the UID of the user as 0, to demonstrate access to the root account.
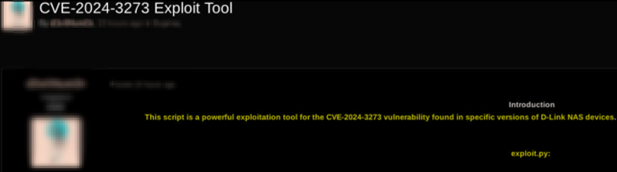
Figure 3 – TA sharing an exploit for CVE-2024-3273 over a cybercrime forum
Vulnerability Details
The vulnerability found in affected versions of D-Link stems from the nas_sharing.cgi CGI script. D-Link has recommended retiring these products and replacing them with products that receive firmware updates, as End of Life (EOL)/End of Support (EOS) products are no longer supported. All firmware development for these products ceases.
Use of Hard-Coded Credentials (CVE-2024-3272)
The vulnerability falls under the critical severity category and allows a remote attacker to manipulate the ‘user’ argument using the input ‘messagebus,’ thus revealing hard-coded credentials.
Command Injection (CVE-2024-3273)
The vulnerability falls under the high severity category and allows a remote attacker to manipulate the ‘system’ parameter, which leads to command injection.
By exploiting both vulnerabilities in tandem, an attacker could effectively execute arbitrary commands on the system. This could result in unauthorized access to sensitive data, alterations to system configurations, or the creation of denial-of-service situations.
Affected Products
- D-Link DNS-320L, DNS-325, DNS-327L and DNS-340L up to 20240403
Internet Exposure of D-Link NAS
At the time of publishing this analysis, Cyble researchers observed that 94,446 internet exposed DLink NAS were exposed over the internet. With majority of instances exposed over the United Kingdom, Thailand, Italy, Germany, and Hungary (as shown below).

Conclusion
The ongoing exploitation of D-Link NAS devices by threat actors, as detected by the CGSI network, represents a troubling development for both public and private organizations. The criticality of the threat emerging from D-Link NAS devices that have reached their End-of-Life (EOL)/End-of-Service (EOS) status, have exposures over the internet, and are readily exploitable due to the availability of public exploits, is extremely catastrophic and can have a cascading effect on the security postures of several organizations.
The vulnerabilities present in NAS devices pose a serious risk, as exploitation not only compromises the integrity and security of the affected device but also extends to other interconnected devices within the network. This interconnectedness amplifies the potential impact, exposing enterprise networks to significant risks and vulnerabilities.
Recommendations
- Upgrade or Replace: Prioritize upgrading to supported versions or replacing EOL/EOS products with newer alternatives that receive regular security updates and patches.
- Segmentation and Isolation: Segregate EOL/EOS products into isolated network segments to minimize their exposure to potential threats and limit their impact on the overall network if compromised.
- Implement Additional Security Measures: Deploy additional security controls such as firewalls, intrusion detection systems (IDS), and network monitoring solutions to enhance the security posture of EOL/EOS products.
- Regular Security Assessments and Monitoring: Conduct regular security assessments and vulnerability scans to identify and address any weaknesses or vulnerabilities in EOL/EOS products. Implement continuous monitoring to detect and respond to security incidents promptly.
- Risk Mitigation Strategies: Develop and implement risk mitigation strategies tailored to EOL/EOS products, including contingency plans for potential security incidents and business continuity measures to minimize disruptions.
- Vendor Communication and Collaboration: Maintain open communication with the vendor to inquire about any potential extended support options, security advisories, or alternative solutions for EOL/EOS products. Collaborate with the vendor and cybersecurity community to address security concerns effectively.
- User Awareness and Training: Provide comprehensive cybersecurity awareness and training programs for users and administrators of EOL/EOS products. Educate them about the risks associated with using unsupported software and emphasize the importance of adhering to security best practices to mitigate those risks effectively.
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| 47[.]94[.]155[.]169 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 8[.]134[.]81[.]86 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 171[.]244[.]23[.]11 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 120[.]79[.]250[.]151 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 35[.]229[.]184[.]234 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 182[.]253[.]115[.]123 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 202[.]79[.]171[.]107 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 116[.]198[.]40[.]76 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 121[.]41[.]56[.]249 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 114[.]67[.]183[.]11 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 183[.]56[.]199[.]229 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 116[.]62[.]192[.]107 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 80[.]94[.]92[.]60 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 91[.]215[.]85[.]61 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 14[.]225[.]53[.]162 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 112[.]111[.]0[.]102 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 186[.]251[.]21[.]234 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 51[.]79[.]19[.]53 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 115[.]220[.]2[.]96 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 39[.]98[.]218[.]14 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 120[.]196[.]56[.]220 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
| 14[.]116[.]254[.]172 | IP Address | IP addresses observed attempting to exploit CVE-2024-3273. |
References
https://github.com/netsecfish/dlink
https://vuldb.com/?id.259284
The post Critical D-Link NAS vulnerability under active exploitation appeared first on Cyble.
React to this headline: