How to Know If You’ve Been Hacked: Signs & Recovery (2024)
These days, cyberattacks aren’t just something that happens to big corporations or government agencies — they can hit anyone, including everyday internet users. Hackers are always finding new ways to steal personal information, hijack accounts, and infect devices with malware.
In recent years, ransomware groups have taken things even further. Conti, a notorious cybercrime group, managed to shut down Costa Rica’s entire government by exploiting a security flaw. Hackers have even targeted hotel guests, locking them out of their rooms remotely until a ransom was paid.
That’s why it’s more important than ever to recognize when you’ve been hacked. The sooner you spot the warning signs, the better chance you have of minimizing damage, protecting your personal data, and getting things back under control. In this guide, I’ll help you identify the most common signs that your accounts or devices might be compromised — and give you practical steps to recover quickly and stay safe going forward.
How to Know If You’ve Been Hacked: 10 Common Warning Signs
Recognizing the early warning signs of a hack is crucial for minimizing damage and protecting your data. These signs can manifest in various ways, often disrupting your usual digital activities. By staying alert to these indicators, you can take swift action to secure your systems and prevent further unauthorized access.
1. Unauthorized Restrictions on Device Access and System Settings
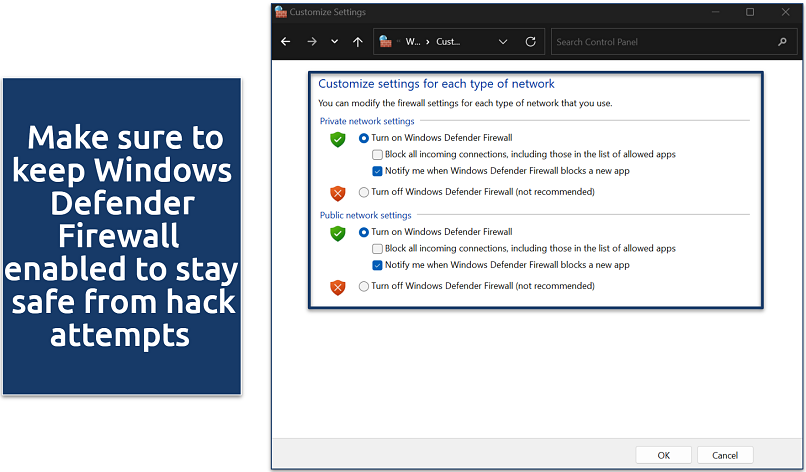
Hackers sometimes tamper with your device’s settings to lock you out or limit access to key functions. This can involve deactivating antivirus software, changing security settings, or even updating passwords to block you from regaining control. If you notice anything unusual, like antivirus or firewall protections being turned off without your input, it could be a sign of unauthorized access.
It’s important to act fast — re-enable your antivirus and firewall and update your passwords right away to secure your device. If your usual passwords stop working, that’s a clear indicator that someone may have taken control. Keeping an eye on your system settings regularly makes it easier to catch and fix these issues before they cause bigger problems.
 Run a complete scan of your PC to ensure there is no malware
Run a complete scan of your PC to ensure there is no malware
2. Unfamiliar Apps Appearing Without Installation
Finding unfamiliar apps on your device can be a strong indicator that malware has made its way in. Hackers may use these apps to steal your personal information or even control your device remotely. Other warning signs of malware include apps crashing frequently, rapid battery drain, and unexpected pop-ups or ads appearing out of nowhere.
It’s a good habit to regularly review your installed apps and remove any that seem suspicious or unfamiliar. On Windows, booting into Safe Mode can help you safely remove any unwanted programs that might not uninstall normally.
 You can also boot into safe mode with command prompt access
You can also boot into safe mode with command prompt access
Running regular scans with reliable antivirus software adds an extra layer of security, helping you detect and remove malicious apps before they cause serious harm. Staying proactive with these checks ensures your device remains safe.
3. Unexplained Cursor Activity and Mouse Clicks
If your mouse moves on its own or clicks things without your input, it could mean hackers are controlling your device using remote access tools. This can also manifest through unauthorized activity on your accounts — like messages you didn’t send, posts you didn’t make, or logins from unknown locations or devices.
To stay safe, turn off remote access features unless you absolutely need them. If you notice strange cursor movements or clicks, disconnect from the internet right away and run a full security scan to detect and remove any remote access tools. Taking these steps quickly helps block hackers from controlling your device and keeps your data secure.
4. Bogus Browser Toolbars and Redirected Searches
If your browser suddenly has new toolbars or your searches get redirected to strange websites, it’s likely a case of browser hijacking. Hackers or malicious software often use these unwanted toolbars to gather your personal data and mess with your browser’s settings—sometimes without you even realizing it.
To fix this, head to your browser settings and remove any unfamiliar or suspicious extensions. You can also restore your browser’s default settings to undo any unwanted changes. Keeping your browser up to date and using trusted security extensions can go a long way in preventing future hijacking attempts. Staying on top of these changes helps keep your browsing experience smooth and secure.
5. Exposure of Your Credentials and Data in a Security Breach
When hackers gain unauthorized access to personal data through breaches, it can lead to identity theft and financial trouble. To check if your credentials have been exposed, you can use services like Have I Been Pwned, which alerts you if your email or passwords are part of a known breach.
Browsers like Chrome offer a handy Password Checkup feature that shows which of your saved passwords have been compromised. If any are flagged, update them immediately to secure your accounts.
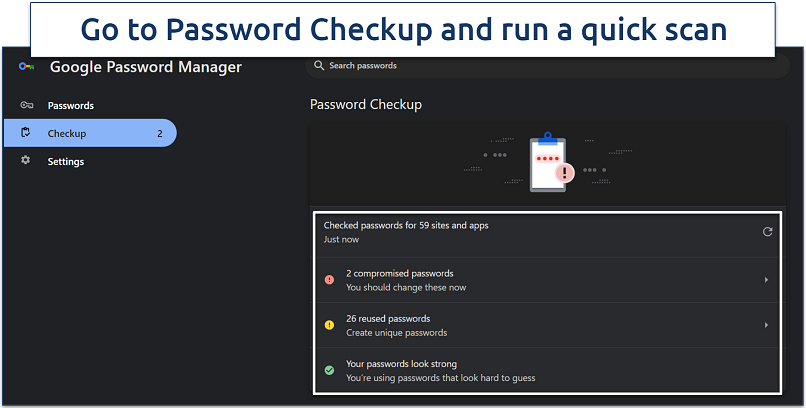 You can quickly change any compromised passwords right from the same window
You can quickly change any compromised passwords right from the same window
For Apple users, similar protection is built into Settings > Passwords. Just enable Detect Compromised Passwords, and your iPhone will notify you if any saved passwords have been leaked.
If you discover your information has been exposed, change your passwords right away and keep an eye on your accounts for unusual activity. Enabling two-factor authentication (2FA) adds an extra layer of security, making it harder for hackers to gain access in the future. Also, be on alert for unexpected password reset emails — these could indicate someone is trying to access your accounts.
6. Being Locked Out of Your Account
Getting locked out of an account, like email or social media, can be frustrating. This usually happens when hackers gain access to your login credentials and change the password to block you from logging back in. If your usual password suddenly doesn’t work, it’s a strong sign that someone else might have taken control.
To recover a locked account, use the account recovery options provided by the service, such as password reset links or security questions. Once you regain access, secure your accounts with strong, unique passwords and enable two-factor authentication to prevent future takeovers. Regularly updating your security settings can also help protect your accounts from unauthorized access.
7. Friends Receiving Messages You Never Sent
If your friends tell you they’ve received strange messages from you, it’s a likely sign your account has been compromised. Hackers often hijack accounts to send spam or phishing links, hoping to trick your contacts into clicking on them.
Notify your contacts immediately to warn them about the potential breach and avoid interacting with suspicious messages. Change your passwords and review your account activity for any unauthorized actions.
8. Abnormal Network Activity and Performance Issues
Unexpected network issues — like slower internet speeds or a sudden spike in data usage — can hint at a compromised system. Hackers sometimes use networks for activities like cryptocurrency mining or data theft, draining resources and slowing down performance.
You can use network analysis tools to track unusual traffic or unauthorized devices connected to your network. To keep your network secure, make sure you use a strong WiFi password and regularly update your router’s firmware. If performance issues persist, run a thorough security scan to detect and remove any malicious software or unauthorized programs.
9. Unusual Alerts for Debit Transactions
Unexpected alerts for debit transactions could mean hackers have accessed your financial information and are making unauthorized purchases. Monitoring your bank statements and enabling transaction alerts is a smart way to spot suspicious activity quickly.
If you notice any unauthorized charges, contact your bank right away to report the fraud and secure your account. Acting fast helps limit financial losses and ensures your sensitive information stays protected from further compromise.
10. Increase in Pop-Ups and Advertisements
A sudden increase in pop-ups or ads on your device can signal an adware or malware infection. This can also lead to other odd behavior, like app crashes, rapid battery drain, or unwanted redirects to malicious websites. Some pop-ups are more than just annoying — they can be dangerous, tricking you into downloading more malware.
To stop pop-ups, tweak your browser settings and install a reliable ad blocker. If you suspect adware is installed, run a full security scan with up-to-date antivirus software to remove it. Keeping your software and security tools updated helps prevent future infections, ensuring a smoother and safer browsing experience.
Pro Tip: A reliable VPN like ExpressVPN masks your IP address by routing your internet traffic through a secure server, making it appear as though you’re browsing from a different location. This hides your real IP address, which hackers could otherwise use to track your online activity, target your network with attacks, or find your physical location.
By encrypting your data along the way, a VPN adds an extra layer of security, making it much harder for hackers to intercept sensitive information — especially when using public WiFi networks. This way, even if someone is trying to snoop on your connection, they’ll only see encrypted data.
Types of Hacks
Knowing how hackers operate is the first step toward protecting your data and devices. Some of the most common hacking techniques include:
- Phishing. Hackers trick you into giving away sensitive information, like passwords or credit card details, by pretending to be someone trustworthy.
- Malware. Malicious software infects your system, causing damage or stealing information.
- Ransomware. This type of malware locks your files and demands a ransom to restore access, as seen with the infamous WannaCry attack.
- Brute force attacks. Hackers try to crack your password by repeatedly guessing combinations.
- Man-in-the-middle attacks. By intercepting your online communications, hackers can steal information or manipulate data being transmitted.
- Grandparent hacks. Hackers target older adults, posing as a grandchild or family member in need of urgent financial help. These scams often take advantage of emotional manipulation, convincing victims to send money or share personal information.
Understanding these threats helps you stay one step ahead and avoid falling victim to such attacks.
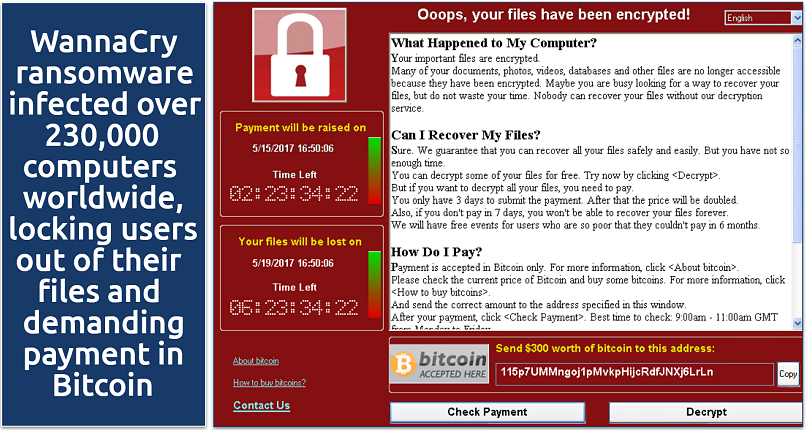 Always back up your files to avoid getting locked out by ransomware attacks like this
Always back up your files to avoid getting locked out by ransomware attacks like this
Email Hacks
When someone gains unauthorized access to your email, it can cause all sorts of trouble. Here are a few common ways email hacks can affect you:
- Unauthorized access. Hackers might use your email to send phishing links or malware to your contacts, making it seem like the messages came from you. This not only puts your contacts at risk but also damages your reputation.
- Password changes. If hackers change your email password, you could be locked out of your account, cutting off access to important messages and information.
- Exposure of sensitive information. Emails often contain personal details, financial information, or even login credentials that hackers can exploit for identity theft or fraud.
- Suspicious activity. Notifications about unfamiliar logins or devices accessing your account are major red flags. If this happens, it’s time to act quickly to secure your account.
Social Media Hacks
Social media hacks can put your personal information and online presence at risk, especially on popular platforms like Facebook, Instagram, TikTok, LinkedIn, Discord, and Roblox. Here are some signs that your account might be compromised:
- Unauthorized posts and messages. Hackers might post content or send messages from your account, damaging your reputation and potentially spreading malware to your contacts.
- Profile changes. If you notice unexpected changes to your profile — like your name, bio, or birthday — it’s a strong sign someone else might have taken control of your account.
- Unauthorized friend or follower requests. Hackers often send requests to random individuals, either to gather more personal information about you or to target your contacts.
- Compromised passwords. Using weak or reused passwords makes it easier for hackers to take over your accounts. Make it a habit to use strong, unique passwords for each platform and change them regularly.
Pro Tip: One safe way to protect your social media data is by using a VPN. Check out our detailed guides:
Mobile Device Hacks
Mobile devices are always connected and run various apps, making them tempting targets for hackers. Here are some signs your phone or tablet might be compromised:
- Unfamiliar apps. Hackers can install apps without your permission, using them to monitor your activity or steal personal data.
- Battery drain. If your battery is depleting unusually fast, malware might be running in the background, consuming resources.
- Unexpected text messages or calls. If your device sends or receives messages or calls that you didn’t initiate, hackers might be using your phone for malicious activities.
- Increase in data usage. A sudden spike in data usage could indicate that your device is transmitting information without your consent, possibly sending your data to hackers.
Computer Hacks
Computer hacks can mess with your daily routine and put your personal data at risk. Here are a few signs that your computer might be compromised:
- Slow performance. If your computer feels sluggish or struggles with simple tasks, malware could be running in the background, using up your system’s resources.
- Unrecognized programs. Hackers might install software without your consent, using it to spy on your activity or steal sensitive data.
- Missing files. Important files may disappear or be encrypted and held for ransom, leaving you locked out of valuable information.
- Unauthorized access. Suspicious login attempts or unexpected changes to settings can mean someone else has taken control of your system.
Banking Hacks
Banking hacks can be especially stressful since they directly impact your finances. Here are some signs that your bank account may have been compromised:
- Unauthorized transactions. Unexpected charges or withdrawals are red flags. If not caught quickly, they can lead to serious financial losses.
- Missing statements. If you stop receiving your regular bank statements, hackers might have changed your contact information to hide their activity.
- Login issues. Trouble accessing your account — like changed passwords or altered security questions — could mean someone else has gained control of your banking details.
If you spot signs that your accounts have been hacked, act quickly to protect yourself. Reach out to your service providers — whether it’s email, social media, or banking — to report the breach and secure your accounts. It’s also a good idea to review your account activity logs for any suspicious behavior. Look for unfamiliar devices or sessions and revoke their access immediately.
What Are the Consequences of Being Hacked?
Getting hacked can have serious consequences that affect both your personal and professional life. Here are some of the most significant ways it can impact you:
Financial Loss
| Direct Theft | Hackers can break into your bank accounts, credit cards, or online payment systems and steal your money directly. |
| Fraudulent Transactions | You might notice unauthorized purchases or transfers, which can quickly add up and cause major financial headaches. |
| Ransom Payments | In ransomware attacks, hackers lock your files or systems and demand a ransom. Many victims feel forced to pay just to get their data back |
Identity Theft
| Personal Information Misuse | Hackers can steal personal information like Social Security numbers, driver’s license details, and medical records, then use it to commit fraud or sell it on the dark web. |
| Credit Score Impact | Fraudulent activities under your name can severely damage your credit score, making it difficult to secure loans or credit in the future. |
Privacy Breach
| Exposure of Sensitive Data | Personal photos, emails, and messages can be leaked, leading to embarrassment, emotional distress, or blackmail. |
| Corporate Espionage | In a business context, confidential information such as trade secrets, customer data, and financial records can be exposed, damaging a company’s reputation and competitive edge. |
Reputational Damage
| Personal Reputation | Private information or sensitive communications can be made public, affecting personal relationships and professional standing. |
| Business Reputation | Data breaches can erode customer trust, lead to negative publicity, and result in the loss of business. |
Operational Disruption
| System Downtime | Hacks can cause significant downtime for systems and networks, disrupting business operations and leading to productivity losses. |
| Recovery Costs | Repairing and restoring systems after an attack can be costly and time-consuming, requiring specialized cybersecurity services. |
Legal and Regulatory Consequences
| Compliance Violations | Businesses that fail to protect customer data may face fines and sanctions for non-compliance with data protection regulations such as GDPR or CCPA. |
| Litigation | Victims of data breaches may face lawsuits from affected parties seeking compensation for damages. |
Psychological Impact
| Stress and Anxiety | The experience of being hacked can cause significant stress and anxiety, particularly if sensitive personal or financial information is compromised. |
| Loss of Trust | Individuals and businesses may become more distrustful of digital technologies and online interactions, affecting their behavior and decision-making. |
Long-Term Consequences
| Ongoing Vulnerability | Once you’ve been hacked, you may remain a target for future attacks, as hackers know your system’s vulnerabilities. |
| Difficulty in Recovery | Restoring your financial, personal, and professional standing after a hack can be a long and arduous process, often requiring substantial effort and resources. |
What to Do If You’ve Been Hacked
Taking swift and decisive action is crucial if you suspect you’ve been hacked. Here’s a detailed step-by-step guide to help you mitigate damage and secure your digital life:
- Check if your password has been compromised and change it immediately. Use a reliable password manager or online service to see if any of your passwords have been exposed to a data breach. If you find compromised passwords, change them immediately. Choose strong, unique combinations for each account, using a mix of letters, numbers, and special characters.
- Secure your finances by freezing your cards and blocking your accounts. Freeze your cards and block any suspicious transactions. Monitor your accounts closely for any unauthorized activities and report them to your bank to prevent further financial loss.
- Disconnect hacked devices from your WiFi network. This prevents the hacker from accessing other devices connected to the same network. This isolation helps contain the breach and limits the hacker’s reach.
- Conduct a malware scan on all devices. Remove any detected malware or suspicious programs to clean your system. Also, use an anti-virus program to scan and detect any hidden malware or viruses.
- Secure your mobile number by locking your SIM. This step prevents unauthorized access to your phone number, which hackers can use for further attacks, such as SIM swapping.
- Investigate unusual account activity. Look for signs of unauthorized access, such as login attempts from unfamiliar locations, changes in account settings, or unfamiliar messages. If you find any suspicious activity, take immediate steps to secure those accounts.
- Unlink online accounts to limit further damage. This includes social media, email, and financial accounts that could be exploited further if linked to a compromised account.
- Warn your friends and family about the security breach. Inform your friends and family about the security breach so they can be cautious of any suspicious messages or requests they might receive from your compromised accounts. This warning helps prevent the hacker from extending their reach to your contacts.
- Perform a full device wipe and clean installation. If you find persistent or severe malware, consider performing a complete device wipe and clean installation of the operating system to ensure all traces of the hack are removed.
- Report the incident to the Federal Trade Commission (FTC). Filing a report with the FTC helps authorities track cybercriminal activities and prevent future incidents. It also provides you with resources and support for recovery.
How to Prevent Hacking
Keeping your data safe from hackers is easier when you take a few proactive steps to secure your digital presence. Here are some effective ways to protect yourself from hacking attempts:
1. Enable Two-Factor Authentication (2FA)
Adding an extra layer of security, 2FA requires you to verify your identity using two methods — usually something you know (like a password) and something you have (like a code sent to your phone). Even if a hacker gets your password, 2FA makes it much harder for them to access your accounts.
2. Use a VPN
A VPN encrypts your internet traffic and hides your IP address, making it difficult for hackers to intercept your data or track your online activities. It’s especially useful when using public WiFi networks, as it protects you from potential threats lurking on unsecured connections. If you’re unsure where to start, check out this guide on how to use the best VPNs to stay safe from hackers.
3. Secure Your WiFi Network
Ensure your WiFi network is encrypted using WPA3 or at least WPA2. Set a strong, unique password for your network and regularly update it. Additionally, consider hiding your network’s SSID to make it less visible to potential attackers.
4. Regularly Update Your Operating System and Software
Keep your operating system, applications, and antivirus software up to date. These updates often include security patches that protect against the latest threats and vulnerabilities.
5. Use a Password Manager
A password manager helps you create and store strong, unique passwords for each of your accounts. This reduces the risk of password reuse and makes it easier to manage your login credentials securely.
6. Set Up Identity Theft Protection and Monitoring Services
Identity theft monitoring services and breach detection tools alert you to suspicious activity involving your personal information. Early detection helps you respond quickly and reduce the chances of identity theft causing long-term damage
7. Establish a Backup “Rescue” Email Address
Use a separate email address solely for account recovery purposes. This email should have a strong password and 2FA enabled, ensuring it remains secure as a backup option for recovering access to your primary accounts.
8. Use Virtual Cards for Online Shopping
Many banks and financial services offer virtual cards, which generate a temporary card number for online purchases. This protects your actual card details from being exposed in the event of a data breach.
9. Turn Off Location Settings in Your Apps
Limit the amount of location data you share by turning off location settings for apps that don’t require it. This reduces the risk of your physical location being tracked or exploited.
10. Enhance Your Device’s Security and Social Media Privacy Settings
Review and adjust your device’s security settings to ensure maximum protection. On social media, update your privacy settings to control who can see your information and posts, minimizing exposure to potential hackers.
11. Uninstall Apps You Don’t Use
Regularly review and uninstall apps that you no longer use. Unnecessary apps can be potential entry points for hackers, especially if they are outdated and lack security updates.
12. Delete Spam Emails Without Opening Them
Avoid opening spam emails or clicking on links within them. Delete such emails immediately to prevent phishing attempts and malware infections.
13. Avoid Using Public WiFi for Sensitive Tasks
Public WiFi networks are often insecure, making it easy for hackers to intercept your data. Avoid accessing sensitive information or conducting financial transactions on public WiFi. If necessary, use a VPN to encrypt your connection.
14. Monitor What You Share on Social Media
Be cautious about the personal information you share on social media platforms. Avoid posting details like your full address, phone number, or travel plans, which can be used by hackers to target you.
FAQs on How to Know If You’ve Been Hacked
How can I check if I’ve been hacked on my phone?
Look for signs such as excessive battery drain, slow performance, unfamiliar apps, high data usage, and unexpected pop-ups. Also, monitor your accounts for suspicious activity and run a malware scan using a reputable security app.
How can I know if I’ve been hacked on my Mac?
Check for signs like unexpected system slowdowns, unusual network activity, frequent crashes, unknown login items, and new applications you didn’t install. Use Mac’s built-in Activity Monitor to spot unfamiliar processes and run a security scan with trusted antivirus software.
How can I know if I’ve been hacked on Facebook and Instagram?
Monitor for unusual activities such as posts you didn’t make, messages you didn’t send, login notifications from unfamiliar locations, and changes to your account information. Check the login activity section in the settings of both apps to review recent logins.
How can I prove someone is hacking my phone and find out exactly who is responsible?
Document unusual activity, such as unexpected apps or settings changes, and use security software to scan for malware. While identifying the exact hacker can be challenging, you can report the incident to your mobile carrier and law enforcement for further investigation.
Is there an app where you can tell if you have been hacked?
Yes, several security apps can help detect if you’ve been hacked, such as Norton Mobile Security, Lookout, and Avast. These apps can scan for malware, monitor for unusual activity, and alert you to potential security breaches. So you can avoid getting your data leaked or information stolen.
You can also work with your email provider to access server logs that include timestamps and IP addresses of all access attempts. Compare these logs with your personal usage to spot any unauthorized access. Also, set up a honeypot by sending a seemingly juicy email to yourself from another address. Monitor any access to the link or attachment in the email, or wait to see if anyone acts on the information.
The Bottom Line: Protect Yourself From Hackers
Hacking is a constant threat, so it’s important to stay proactive about keeping your information safe. Simple steps like turning on two-factor authentication, securing your WiFi, keeping your software up to date, and using a password manager can go a long way in reducing your risk.
Staying vigilant and keeping up with the latest threats will help you spot suspicious activity early and respond quickly. Protecting yourself from hackers isn’t just about avoiding a headache — it’s about safeguarding your privacy, security, and peace of mind in today’s digital world.


React to this headline: