Geopolitical Cyber Warfare: A Look Into the Biggest Attacks
With governments, businesses, and organizations relying increasingly on digital systems, hacking incidents have grown more widespread and systematic. Coordinated cyberattacks have targeted organizations, critical infrastructure, political figures, and even private citizens.
These attacks can disrupt a country’s operations as much as a physical offensive would, so it’s important to study its effects and how these conflicts shape the world we live in. This is why my colleagues at vpnMentor and I looked at cyber warfare attacks related to four major geopolitical conflicts:
Our team reviewed records of the most notable incidents between these countries up to the first half of 2024, and we derived analyses and conclusions from the collated data. Our goal was to assess the trends and the potential impacts these attacks have on governments, organizations, and individuals.
For this research, we only considered incidents acknowledged by the victim countries or regarded as heavily motivated by geopolitical conflicts. We also included attacks suspected to be carried out or sponsored by governments allied with countries in conflict. Unconfirmed or nondescript attacks were disregarded.
Trends in the Most Notable State-Backed Cyberattacks
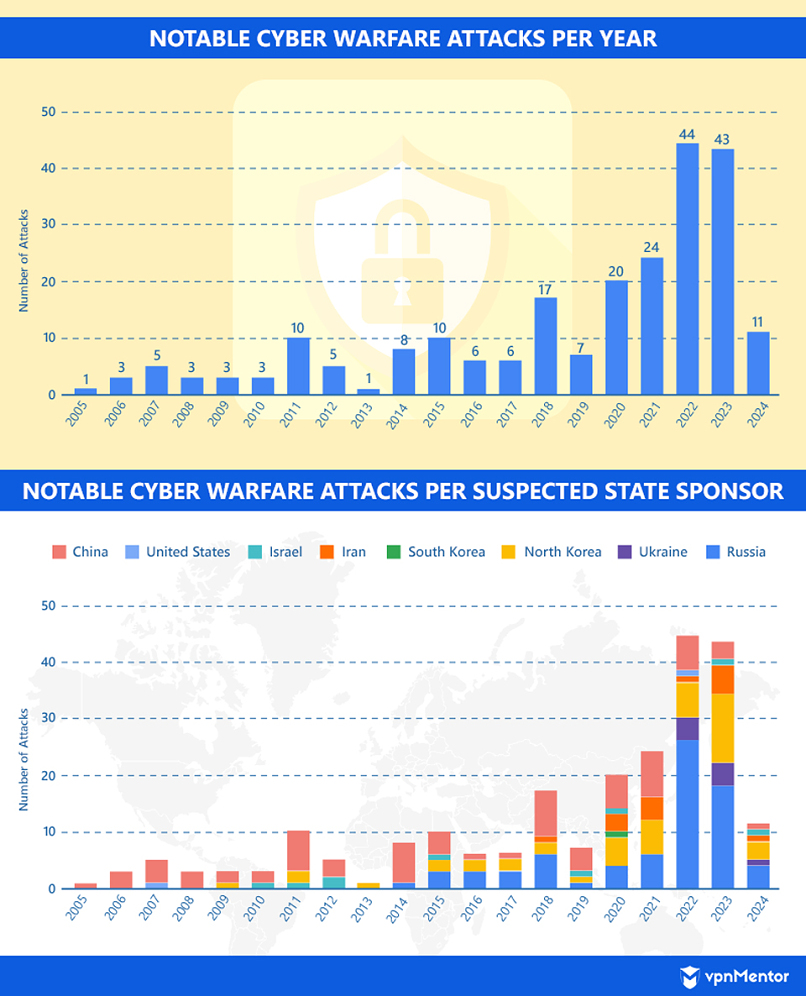
Instances of politically motivated cyberattacks between feuding countries have grown significantly since the mid-2000s. The first notable spike came in 2018 when suspected Russia-backed hackers intensified their attacks against Ukraine. At the same time, Chinese threat actors increased their attacks against the United States.
While there was a temporary lull in incidents in 2019, cyber warfare seems to be on the rise, with over 40 major incidents recorded in both 2022 and 2023.
The greatest number of cyber warfare attacks launched by a single country in a year is attributed to Russia. Its government is believed to have sponsored at least 26 major cyberattacks against Ukraine in 2022, coinciding with Russia’s invasion of the latter. Since then, Russia has remained the leader in terms of the number of cyber warfare attacks conducted per year.
However, Ukraine is not the only country experiencing a significant onslaught. Since 2022, South Korea has followed behind Ukraine in the number of attacks received.
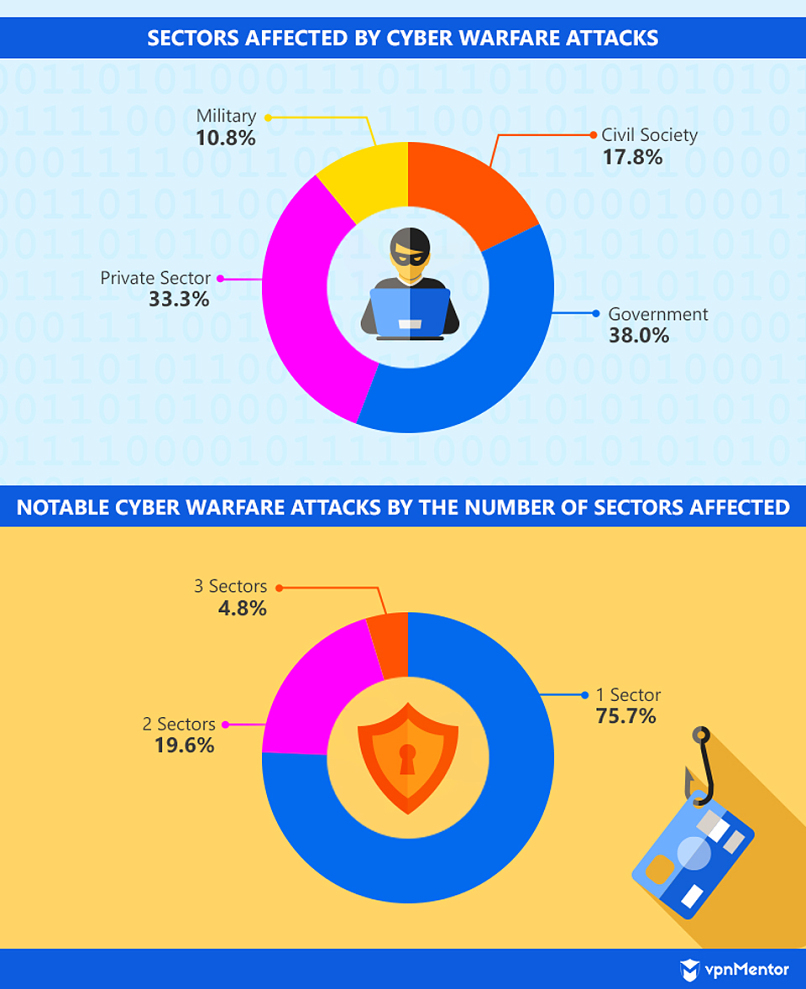
The incidents we studied typically targeted the government, private sector, civil society, and/or military of the victim countries. None of the attacks we found targeted all four sectors at once. Most only affected one, while considerably fewer targeted two or three groups.
Incidents involving military institutions and personnel are the least common. Moreover, civil society attacks never coincided with military attacks. Presumably, this is because military targets have potentially more robust data-breach and hacking protection systems that require more sophisticated methods to compromise.
Government and private sector infrastructures are targeted more often, possibly because they have the potential for the biggest impact on both citizens and official operations.
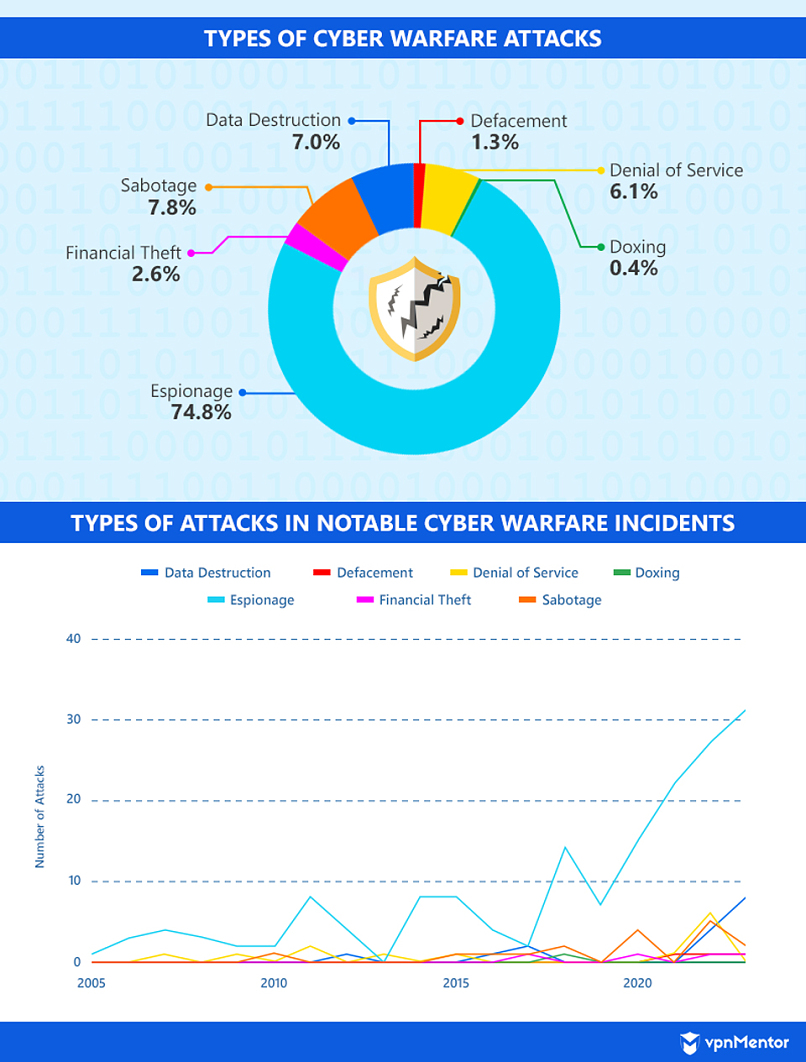
While the frequency of other types of attacks remained more or less consistent and was generally proportional to the number of attacks in a year, espionage cases saw drastic dips and spikes throughout the years. Notable increases were seen in 2011, 2014, and 2018. After a mild drop in 2019, espionage incidents have been consistently increasing.
Around 68% of espionage cases affect civil society, the private sector, or both. This suggests the privacy and security of citizens are potentially compromised because of hostilities between countries.
The Most Notable Geopolitical Conflicts Employing Cyber Warfare
Below, we trace the biggest-impact attacks between four pairs of countries and examine noteworthy trends in cyber warfare activities.
Russia vs. Ukraine
The conflict between Russia and Ukraine goes back to 2014, when Russia annexed Crimea and supported separatists in the Donbas conflict. Even then, Russia had already begun launching cyber warfare attacks against Ukraine that were largely espionage missions.
Things escalated over the next few years when the suspected Russian-sponsored threat actor Sandworm began conducting widely disruptive and destructive cyber campaigns against Ukraine. These included sabotages and data destruction involving Ukrainian banks and electric companies. The attacks caused widespread power outages and temporary failures of financial systems.
2017 was arguably one of the most devastating years for Ukraine in terms of cyber crimes. Three infamous campaigns — NotPetya, BugDrop, and Bad Rabbit — garnered international attention.
NotPetya reportedly disrupted at least 300 companies in Ukraine and many others globally, with an estimated total damage of 10 billion USD. Similarly, the Bad Rabbit malware affected many nations but wreaked the most havoc on Ukrainian payment networks, metro systems, and airport operations. On the other hand, BugDrop gave threat actors remote access to computer microphones, allowing them to gather potentially sensitive data from their targets’ conversations.
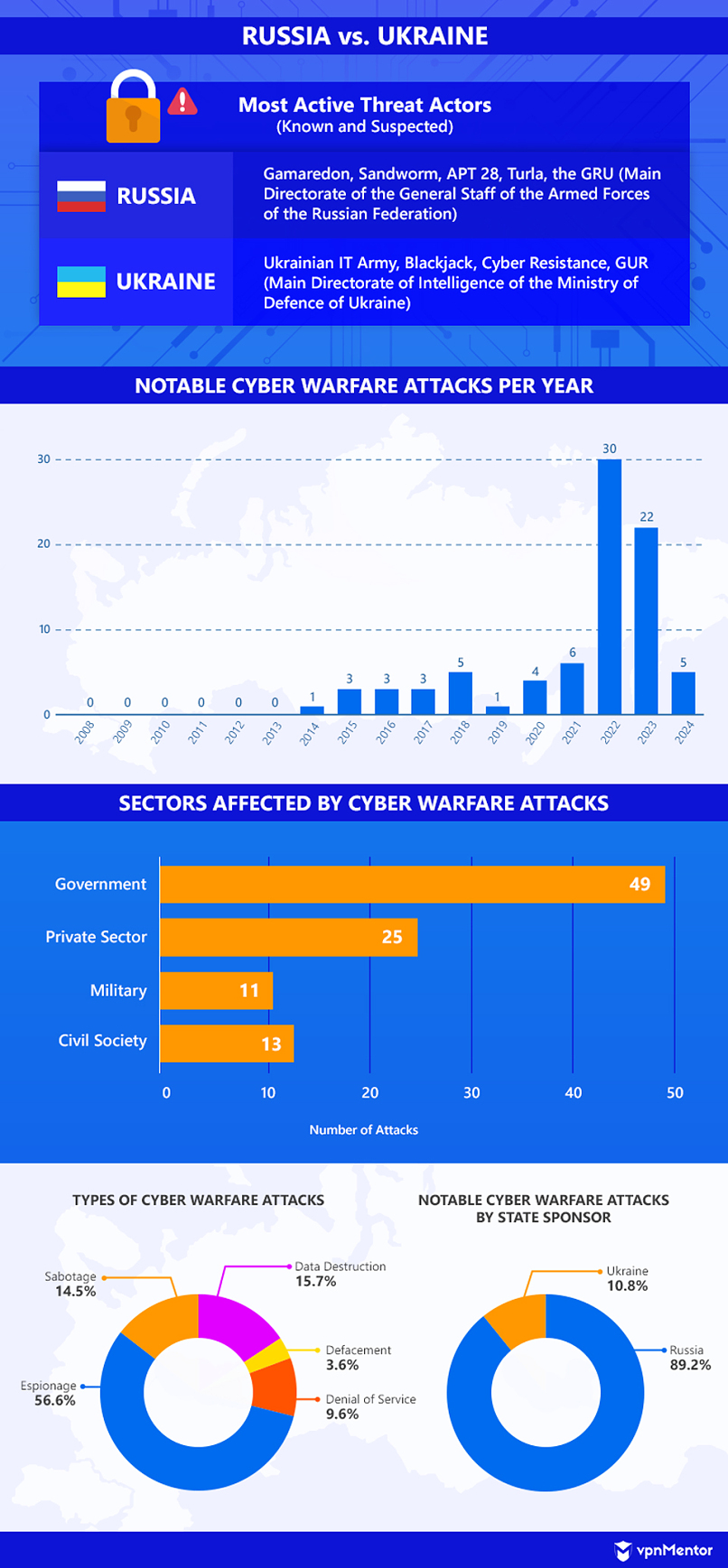
Cyber warfare attacks between these two countries have been ongoing since 2014. However, incidents drastically increased when Russia invaded Ukraine in 2022. Ukrainian hacker groups also emerged that year, focusing initially on Distributed Denial of Service (DDoS) attacks against Russian networks and websites.
Suspected Russia-sponsored threat actors also increased the frequency of attacks. Hackers most prevalently used wipers — malware designed to permanently corrupt or delete files in affected systems — against Ukrainian assets. They often targeted telecommunications companies, internet providers, and media and news agencies. These attacks are believed to be bids to hinder communication and impede war efforts.
Analysts noted that Russia’s 2022 wiper barrage against Ukraine set an all-time record for the most wiper malware codes deployed. Cybersecurity company Fortinet found 16 wiper “families” deployed in Ukraine using a multitude of programming languages. Russian threat actors often disguised them as ransomware despite having purely destructive intentions.
Phishing and DDoS attacks have also targeted Ukrainian government sites and networks, as well as organizations and systems dedicated to the ongoing conflict (military, aid distribution, emergency response, etc.).
While Russia has increased its cyber warfare attacks since 2022, analysts noted that the country could have “swapped quality for quantity,” focusing on persistent and destructive yet relatively straightforward attacks. For instance, none of the cyber warfare tactics deployed against Ukraine in 2022 came close to the code sophistication and destructive power of NotPetya and Bad Rabbit in 2017.
Since the invasion in 2022, other countries have been presumably involved in the cyber warfare between Russia and Ukraine. Belarus is believed to have sponsored at least three attacks against Ukraine in support of Russia. On the other hand, Russian hackers have also targeted other nations in support of Ukraine, such as the United States. Notably, Russian hackers intercepted German military communications about aid distribution in Ukraine in 2024.
Meanwhile, Ukrainian threat actors have been stepping up their attacks. Hackers have been launching an increasing number of cyber campaigns against Russia since late 2023. A notable incident in April 2024 saw the ruling party, United Russia, uncharacteristically admit to being affected by a DDoS attack conducted by Ukraine’s GUR.
North Korea vs. South Korea
North and South Korea have been in a technical war since 1953, when the North Korean invasion ended in an armistice. The long-standing conflict means that cyber hostilities between the two nations also go back a long way. Major incidents were first reported in the late 2000s after North Korea conducted a series of DDoS attacks against websites in South Korea and the United States.
Most of the 2010s saw North Korea launch few but consistent cyber campaigns — mostly espionage operations. During this period, the most impactful incidents include the theft of data detailing military plans in case of an invasion, ransomware that compromised networks in many countries, and the doxing of around 1,000 North Koreans who defected to the South.
In 2018, Russia and China were also suspected to have sponsored separate attacks against South Korea in support of North Korea. The attacks coincided with the meeting between former United States President Donald Trump and Kim Jong-Un, North Korea’s leader.
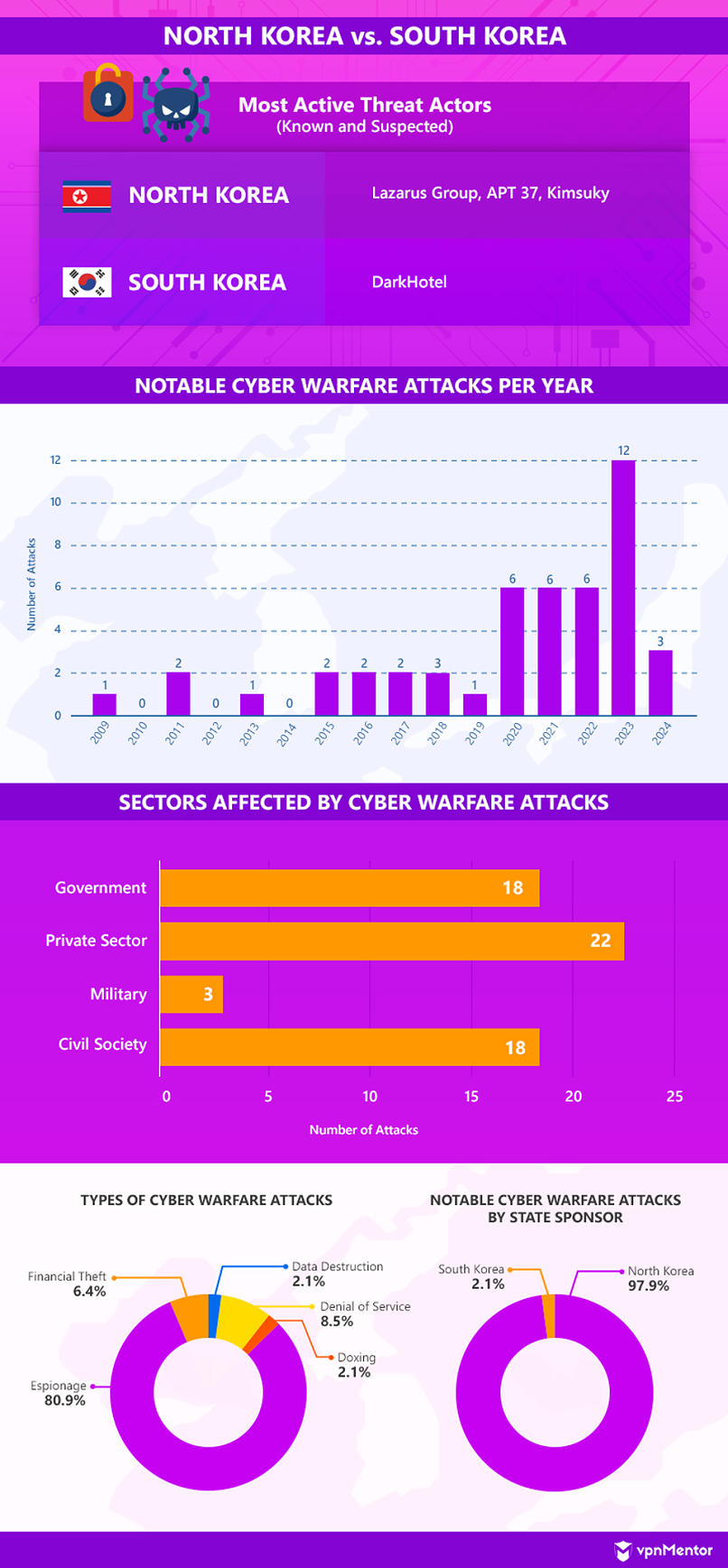
Cyber hostilities started increasing in 2020, with both North and South Korea launching campaigns against one another. North Korean hackers also started becoming more active, with names like the Lazarus Group and Kimsuky leading several attacks every year.
Moreover, a United States military report in 2020 revealed that North Korea’s Bureau 121 — its dedicated cyber warfare unit — has grown to at least 6,000 personnel operating from different countries. Since 2020, cyber warfare tactics between the two countries have mostly focused on espionage operations, with only two major cases of financial theft (ransomware) recorded.
One of the most notable cases came to light in May 2024, when South Korean police claimed that North Korean hackers had stolen over 1 TB of data through a compromised court computer for over two years, starting in January 2021. The data breach allegedly affected citizen’s personal debt and marriage records. Only 4.7 GB of data (over 5,100 documents) have reportedly been recovered and identified so far.
There was a significant spike in North Korea’s cyber warfare activities in 2023. This could potentially be linked to the threat of additional sanctions from the United Nations. North Korea is allegedly using cyber espionage to steal information about South Korea’s vital industries in an attempt to manufacture their own products should sanctions prevent them from importing.
Russia and China vetoed the last sanctions proposed against North Korea in 2022, but the possibility of more sanctions is seemingly spurring the country into action. South Korean analysts and government officials are again on alert in 2024, as three separate attacks targeted the country’s vital defense and manufacturing industries in the first half of the year.
The first came at the beginning of the year when suspected North Korean threat actors used ransomware to extort healthcare companies and other sectors in South Korea and the United States to allegedly obtain more funding for cyberattacks. Later, hackers were reported to have compromised South Korean semiconductor manufacturing companies and defense contractors, stealing product blueprints and information on war tanks and spy planes.
Iran vs. Israel
The conflict between Iran and Israel is more commonly referred to as the Iran–Israel proxy war, as it impacts each country’s relations with nations allied with the other. For instance, Iran has been known to support militias and groups that go against Israel, and Israel has directly attacked Iran’s allies.
While the situation may suggest that more nations would be involved in the cyber war between the two countries, technological capabilities potentially hinder such efforts. Only the United States, a close ally of Israel, has been known to be or suspected of conducting cyberattacks against Iran’s governments and allies.
In the first recorded cyber warfare attack between these two countries, Israel was believed to have received direct help from the United States. This attack in 2010 became known as Operation Olympic Games, which used the infamous Stuxnet virus. The virus reportedly damaged 1,000 to 9,000 gas centrifuges at the Natanz nuclear facility in Iran, substantially damaging Iran’s nuclear program.
Between 2010 and 2015, Iran continued to be on the receiving end of different malware systems and tools that compromised networks for cyber espionage purposes. Equation Group, a threat actor widely suspected of being directly sanctioned by the United States government, is believed to be behind most of these viruses.
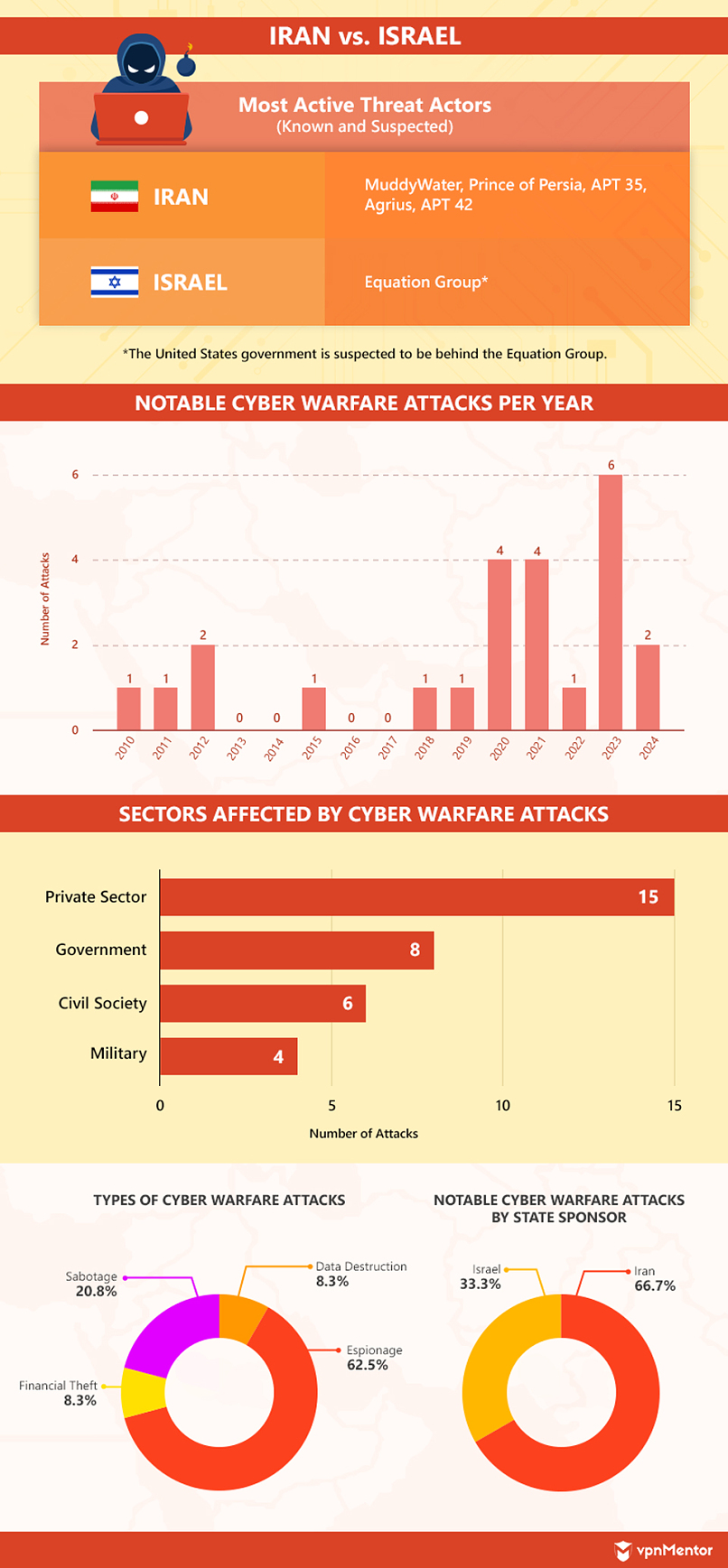
Likely in response to the barrage of attacks, Iran invested heavily in its cyber warfare capabilities. From 2012 to 2015, Iran’s cyber security budget increased by 1,200%. In the following years, the two countries traded blows in cyberspace. Iran has also launched many attacks against the United States.
Despite this pair being the closest to “balanced” in terms of the number of notable attacks by state sponsors, Iran is ahead in terms of the number of major attacks launched. Israeli Prime Minister Benjamin Netanyahu alleged in 2019 that Iranian threat actors are consistently targeting Israeli networks and infrastructure. In our study of notable incidents, Iran has launched double the number of attacks than Israel.
Some of Iran’s biggest cyber warfare activities against Israel and the United States include the Mabna Institute’s alleged hacking of 144 United States universities (as well as 176 universities in other countries), the compromising of over 240 email addresses linked to journalism and presidential elections in the United States, and the attempted sabotage of Israeli water and sewage utilities.
Iranian threat actors are also believed to have conducted a 10-month cyber espionage operation in 2023. The hacker group Agrius reportedly compromised several tech and education firms in Israel, stealing intellectual property and deploying wipers to eliminate their footprint.
One of Israel’s most notable retaliations is its attack on Iran’s Shahid Rajaee Port, crashing the facility’s network and causing disarray and disruption. Suspected Israel-backed hackers also claimed credit for an attack that crippled 70% of gas stations in Iran in December 2023.
In 2024, Iran-linked groups claimed to have hacked a nuclear facility in Israel, allegedly stealing and publishing emails, PowerPoint slides, and PDFs containing sensitive information. Months later, Israeli threat actors paralyzed Iran’s banking systems, including the Central Bank of Iran. The attack was potentially made in response to reports that Iranian hackers were allegedly trying to compromise the United States elections.
United States vs. China
Of the countries included in this study, the United States and China are the only pair with no official direct or indirect conflict. According to the US Department of State, their relationship could be more accurately described as a “strategic competition.” Disputes between them are largely focused on China’s relations with other countries and, arguably, the natural rivalry between the two powers.
As such, some of the earliest cyber warfare attacks recorded happened between the United States and China. In fact, one of the longest-active state-backed threat actors is China’s PLA Unit 61398.
In 2005, the hacker group launched a series of cyber activities that compromised the networks of government agencies in the United States, including the Departments of Homeland Security and State. This campaign, dubbed “Titan Rain,” was the first Chinese cyber espionage operation revealed to the public.
Over the next few years, suspected China-sponsored hackers would continue to target the United States government and military branches, such as the US Department of Defense (DoD), NASA, Naval War College, and National Defense University. Meanwhile, the United States was believed to have conducted at least one DDoS attack against Chinese government networks during this period.
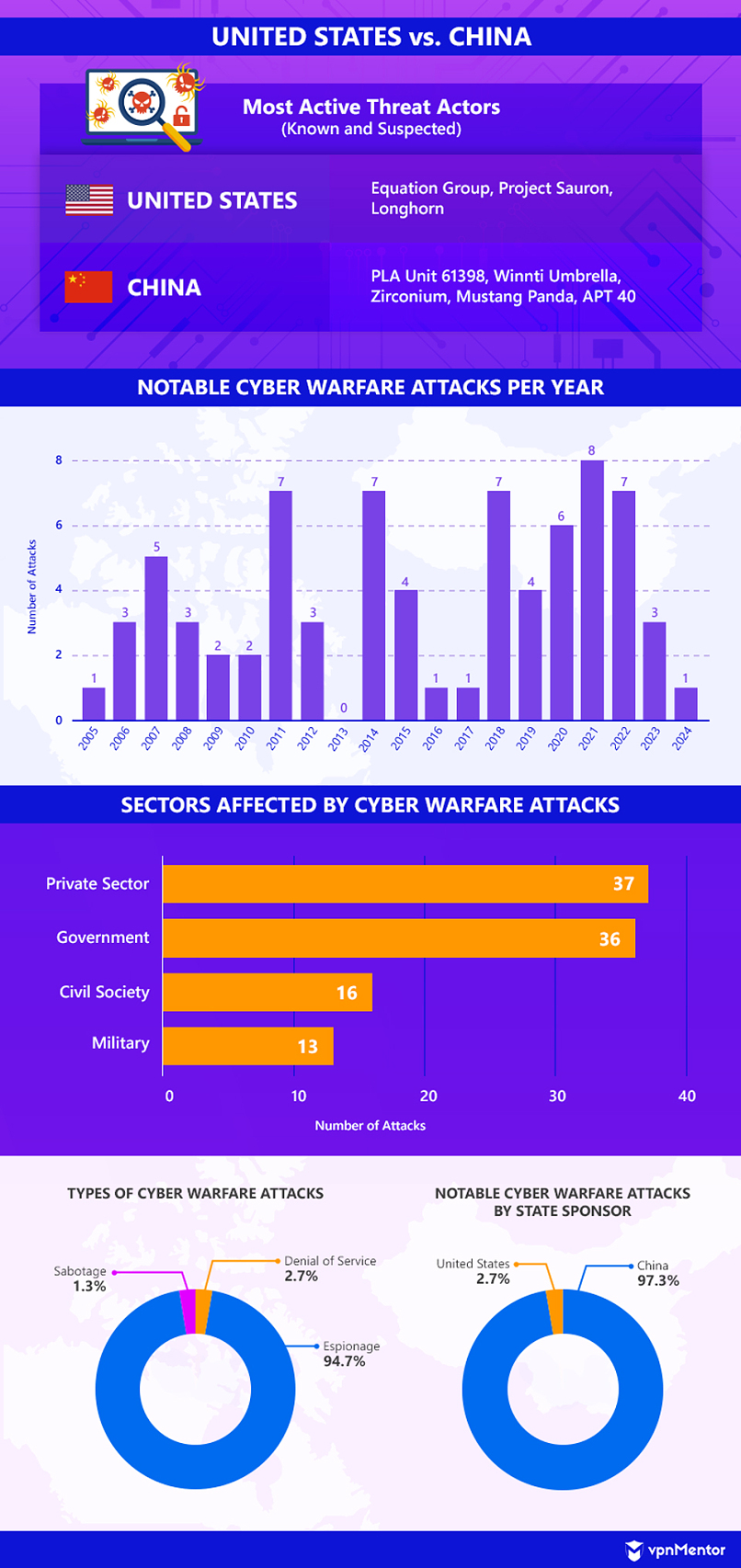
According to the records, most of the major cyberattacks between the two countries have been dealt by China. From 2008 to 2021, no notable cyber warfare attacks against China were attributed to the United States. In 2022, the Chinese government accused the US National Security Agency (NSA) of conducting espionage operations against a defense research university in China, but analysts doubt the claim.
The United States’ official response to cyber warfare attacks seems generally more focused on criminal investigations and indictments. The country often deploys the US Cyber Command to engage in global coalitions to take down malware systems or hacker groups.
That said, at least three high-profile threat actors have been suspected of being backed or sanctioned by the United States: Equation Group, Project Sauron, and Longhorn. All three groups have been linked to cyberattack attempts in China and a number of other countries. Most controversial, perhaps, is Longhorn, which is believed to have been active since 2007 and has targeted 16 different nations. In 2017, reports surfaced claiming that Longhorn is operated by the United States’ Central Intelligence Agency (CIA).
The most impactful Chinese cyber incursions into United States networks and infrastructure include several recurrent attacks on United States federal agencies — such as the Chamber of Commerce, Postal Service, Office of Personnel Management, and Department of Agriculture — as well as private companies and civil society institutions. Also, the alleged China-sponsored APT 41 reportedly stole 20 million USD in COVID relief funds in 2022.
Moreover, China is suspected of being behind many long-running espionage campaigns against the United States, including Operation Aurora (which targeted private tech, chemical, and financial companies) and a year-long cyber operation against at least six state governments. Hackers have also successfully stolen terabytes of data from United States organizations, defense contractors, and military institutions.
Since 2023, the United States has been on alert about a threat called Volt Typhoon, which has been attributed to China. In April 2024, the director of the Federal Bureau of Investigation (FBI) claimed that Volt Typhoon has already compromised critical United States infrastructure and is simply waiting “to deal a devastating blow.”
Analysis: The Impact of Global Politics on the Digital Space
Continued advancements in cyber operations have evidently affected how nations leverage digital technology. While cyberspace allows governments and industries to improve their effectiveness on several fronts, it also opens up significant vulnerabilities. As such, countries must fortify their network security and stay up-to-date with emerging technology to the best of their ability.
Some nations may lack the financial capacity to invest in cybersecurity. However, these nations may not be as vulnerable to cyber warfare attacks as developed countries. Countries capable of engaging in cyber warfare are potentially more susceptible to state-backed cyber intrusions and counterattacks.
The more complex a country’s digital network is, the more likely there are vulnerabilities that can be exploited, especially with the continuous, rapid developments in this area.
Our team finds these insights to merit further study, as cyber warfare attacks — especially espionage operations — often affect civilian citizens. As seen in our research, attacks against military institutions are relatively limited compared to incidents involving government, private sector, or civil society networks. This potentially exposes individuals’ sensitive data to leaks and doxing. Cyberattacks may even compromise vital civilian infrastructure, such as utility companies and telecommunications providers.
Individuals in vulnerable nations should protect their data against potential theft or compromise. Simple actions like being vigilant against phishing, using strong passwords, and encrypting sensitive or important files are already helpful. Additional measures such as using a data deletion service are also advisable. Likewise, governments, organizations, and businesses are responsible for protecting the information of their citizens, partners, or customers.
React to this headline: